Introduction:
Imagine this…
A developer quickly deploys a cloud app.
An S3 bucket is left public.
An IAM policy is over-permissive.
A small SSRF bug is ignored.
💥 Boom — attacker gets access, pivots, escalates, and owns the cloud account.
This is not theory.
This is how real cloud breaches happen.
In this article, we’ll break down real-world cloud attack paths step-by-step from a hacker’s mindset, in simple language, so even beginners and non-IT students can understand:
How attackers think
Where misconfigurations happen
How one small mistake leads to total compromise
If you’re starting cybersecurity, cloud security, or bug bounty — this article is gold.
Why Cloud Misconfigurations Are a Hacker’s Favorite Entry Point

Cloud platforms like AWS, Azure, and GCP are powerful — but security is shared responsibility.
👉 Cloud providers secure the infrastructure
👉 YOU secure configurations
Most companies fail at the second part.
Why attackers love cloud misconfigs:
No exploit chains needed
No malware required
No zero-days
Just logic + permissions + curiosity
🔍 People Also Ask (PAA) – Cloud Security (Beginner Friendly)
What are cloud misconfigurations in cybersecurity?
Cloud misconfigurations are incorrect or insecure cloud settings that expose systems to attackers. Common examples include public S3 buckets, over-permissive IAM roles, exposed API keys, and unsecured cloud metadata access. These mistakes are one of the top causes of real-world cloud breaches.
Why are S3 buckets frequently hacked?
S3 buckets are often hacked because they are accidentally left public by developers. Attackers scan the internet for open buckets and frequently find sensitive data like backups, logs, credentials, and user information. No hacking tools are required — just misconfiguration.
How does SSRF lead to cloud account compromise?
In cloud environments, SSRF can allow attackers to access the cloud metadata service, which stores temporary credentials. Once attackers steal these credentials, they can interact with cloud APIs and sometimes gain full control over cloud resources.
What is IAM abuse in cloud security?
IAM abuse happens when attackers exploit excessive permissions assigned to cloud users or roles. If a compromised role has more permissions than necessary, attackers can escalate privileges, create new users, and maintain long-term access.
Are cloud security issues common in real-world attacks?
Yes. Many major data breaches happen due to simple cloud misconfigurations, not advanced exploits. Attackers prefer cloud issues because they are easy to find, hard to detect, and often give high-impact access with minimal effort.
Attack Path #1: Public S3 Buckets — The Classic Beginner Mistake
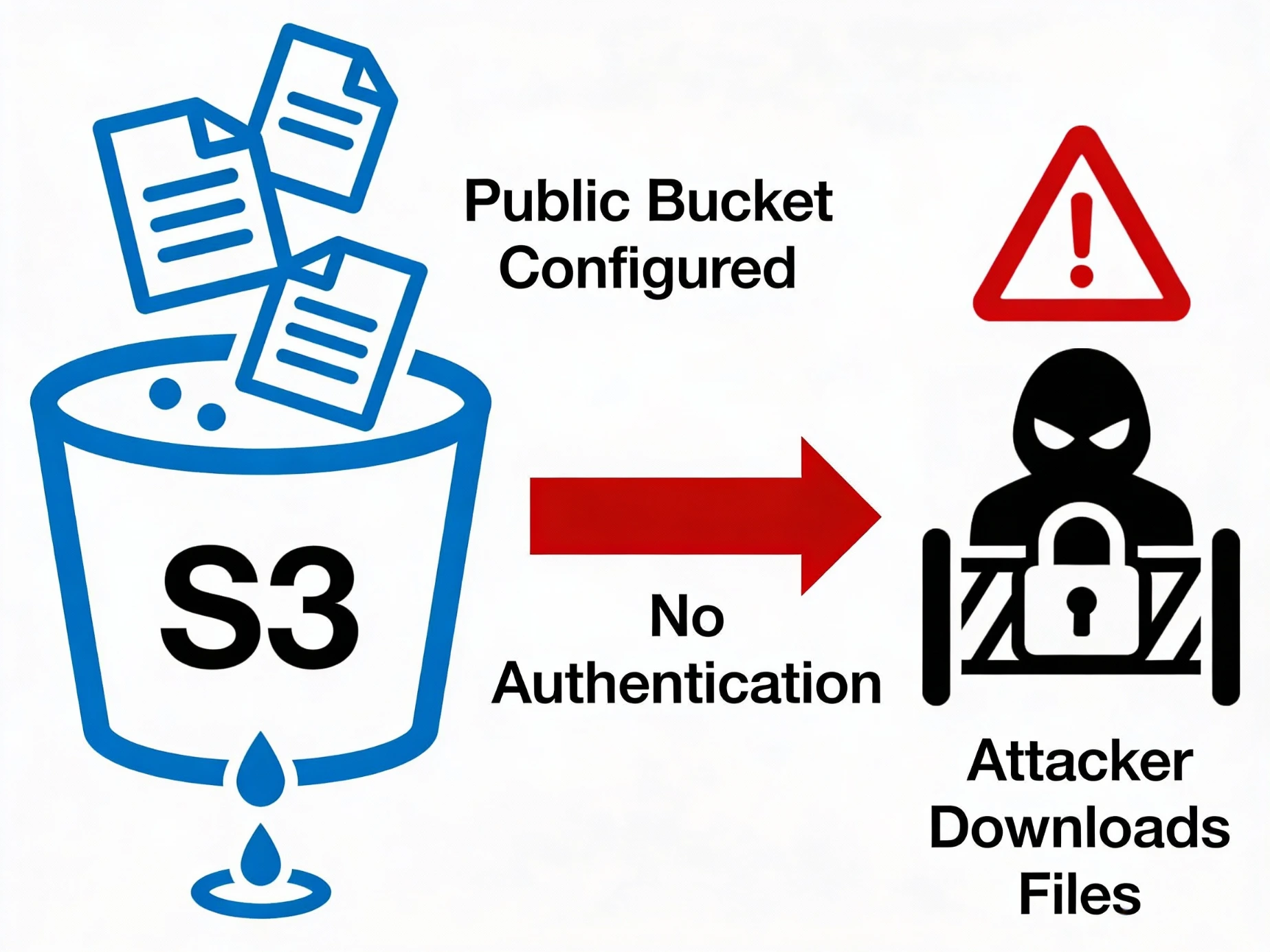
What is an S3 Bucket?
An S3 bucket is cloud storage used for:
User uploads
Logs
Backups
Source code
Configuration files
The Misconfiguration:
Bucket is publicly readable
Sometimes even publicly writable
Hacker’s Perspective 🧠
“Let me check if this company forgot to lock their storage…”
Real-World Impact:
Attackers often find:
.env files (API keys, secrets)
Database backups
Internal documents
User PII data
📌 One exposed bucket = data breach + compliance violation
Attack Path #2: IAM Abuse — When Permissions Become Weapons
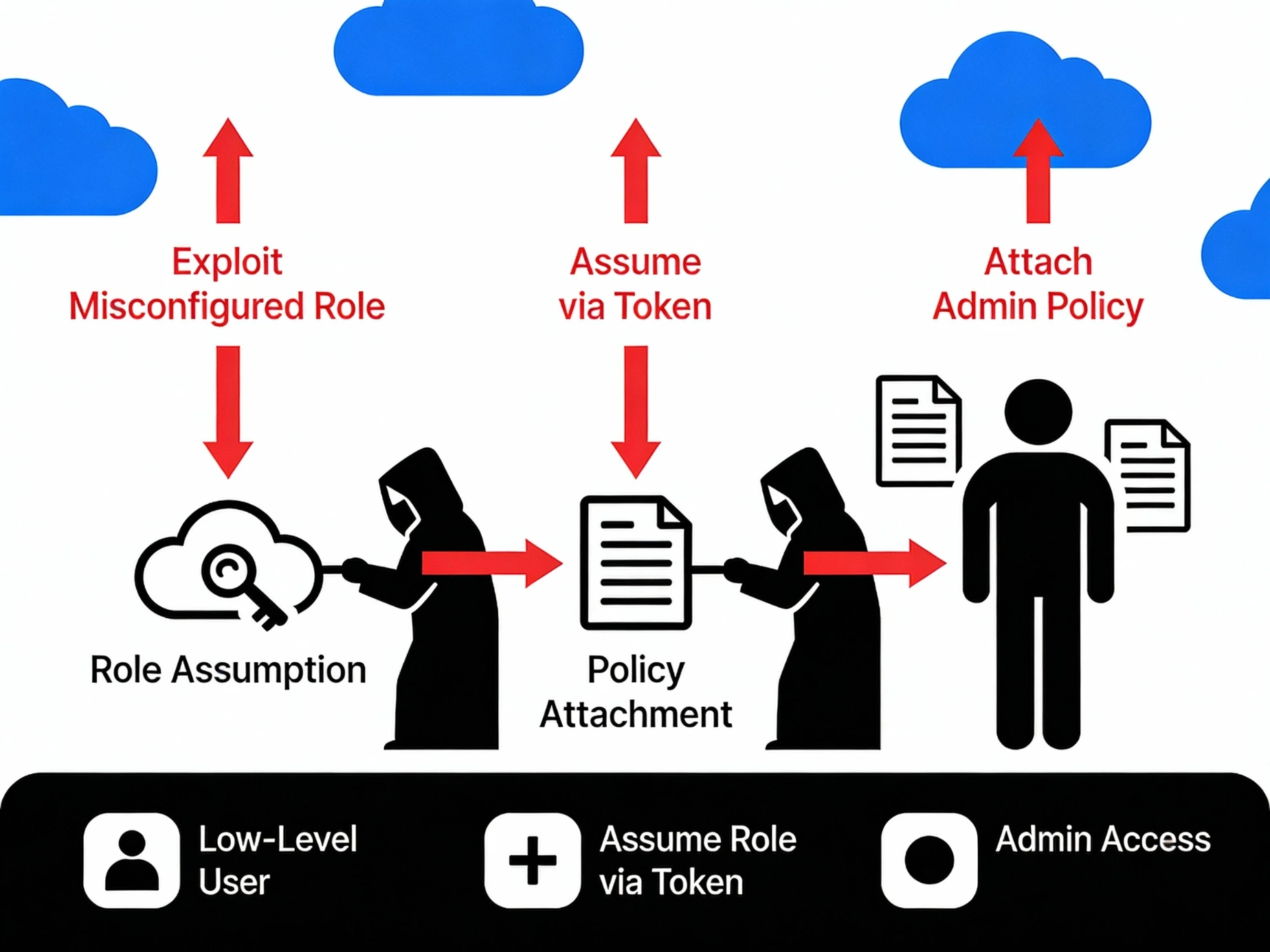
What is IAM?
Identity and Access Management (IAM) controls:
Who can access what
What actions are allowed
The Misconfiguration:
Over-privileged roles
Wildcards like *:*
Unused service roles left active
Hacker’s Perspective 🧠
“If I compromise this one role, how far can I go?”
Typical Exploitation Flow:
Attacker gains low-level access
Lists IAM permissions
Finds privilege escalation path
Becomes admin
Creates backdoor users
🔥 This is how attackers go from small bug → full cloud takeover
Attack Path #3: SSRF → Cloud Metadata → Account Compromise
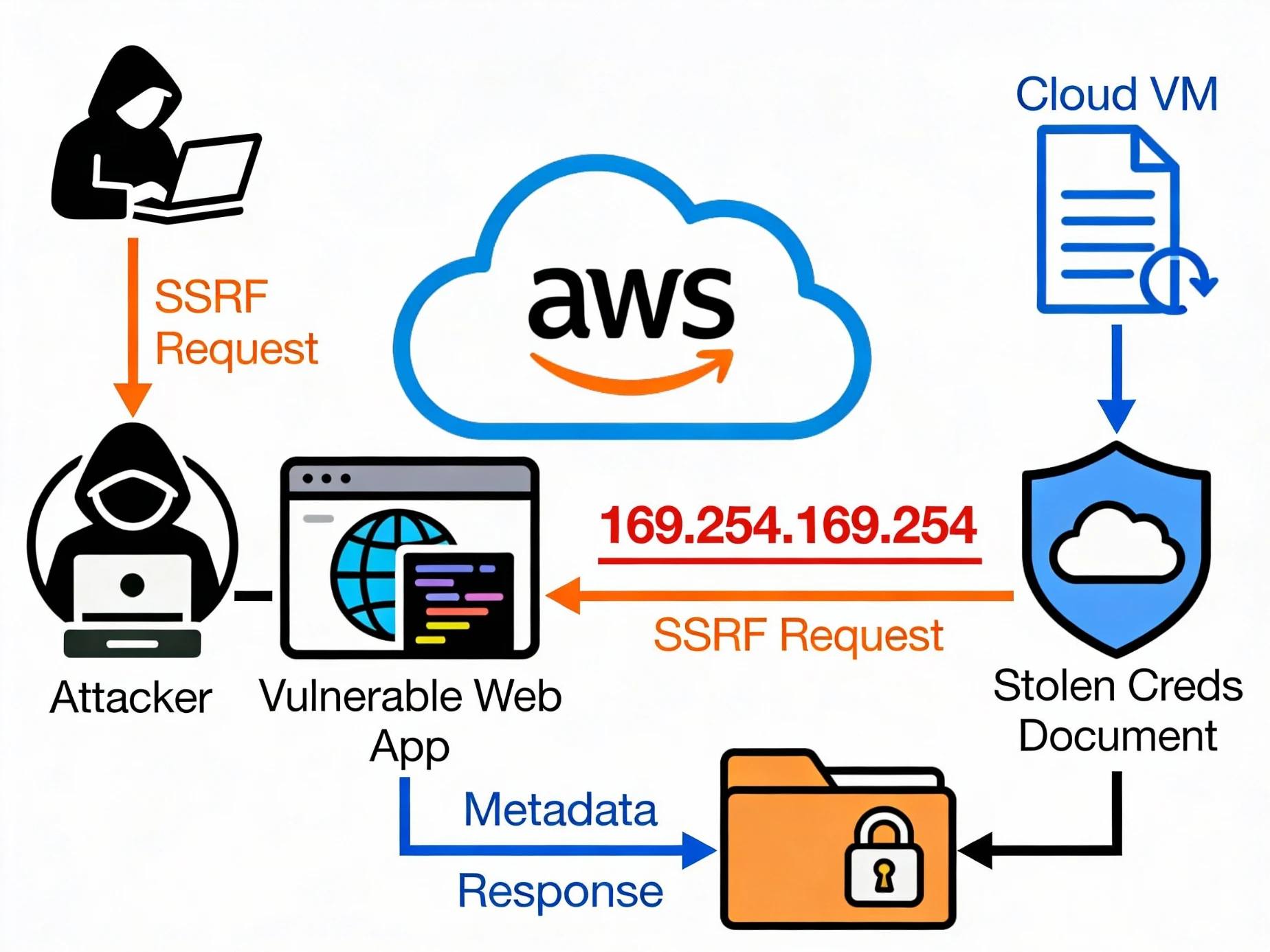
This is one of the most dangerous and misunderstood attack paths.
What is SSRF?
Server-Side Request Forgery (SSRF) lets attackers force the server to make internal requests.
Cloud Metadata Service:
Cloud VMs expose credentials at:
http://169.254.169.254/
Hacker’s Perspective 🧠
“If the server can talk to metadata, maybe I can too…”
Real-World Exploit Chain:
Find SSRF vulnerability
Access metadata endpoint
Steal temporary IAM credentials
Access cloud APIs
Escalate privileges
🚨 This has caused massive real-world breaches
Attack Path #4: Hardcoded Secrets in Cloud Repos
The Mistake:
API keys in GitHub
Secrets in CI/CD configs
Tokens in frontend code
Hacker’s Perspective 🧠
“Let me search GitHub dorks for this company…”
What Attackers Do:
Scan public repos
Test exposed keys
Access cloud services silently
💡 Many breaches start with leaked secrets, not hacking see in movies
Attack Path #5: Chaining Everything Together (The Real Danger)
Real attackers don’t stop at one bug.
Example Real-World Chain:
Public S3 bucket → config file
Config file → API key
API key → IAM role
IAM role → Admin access
Admin → Persistence + data exfiltration
🎯 This is called an “attack path” — and cloud is full of them
Why Beginners MUST Learn Cloud Attack Paths Early
If you’re a:
Student
Beginner in cybersecurity
Bug bounty learner
Non-IT professional switching careers
👉 Cloud security knowledge = high demand + high salary
India + Global Job Reality:
Cloud security roles growing fast
Bug bounty programs reward cloud bugs highly
Companies struggle to find skilled cloud defenders
How to Start Learning This the Right Way (Beginner Friendly)
You don’t need:
❌ Advanced coding
❌ Expensive labs
❌ 10 certifications
You need:
✅ Clear fundamentals
✅ Real-world attack mindset
✅ Hands-on practice
Learn Cloud Security & Bug Bounty with Bugitrix 🚀
At Bugitrix.com, we focus on:
Beginner-friendly cybersecurity
Real-world attack scenarios
Bug bounty mindset
Cloud & web security explained simply
What You’ll Find:
✔ Practical tutorials
✔ Real attack case studies
✔ Free & premium learning resources
✔ Step-by-step guidance (no confusion)
🌐 Visit: https://bugitrix.com
Free Resources & Community (Highly Recommended)
📢 Join our Telegram channel for:
Free cybersecurity resources
Bug bounty tips
Cloud security notes
Beginner roadmaps
👉 Search Telegram: Bugitrix
(or follow links from Bugitrix.com)
❓ Frequently Asked Questions (FAQ)
Is cloud security hard for beginners to learn?
No. Cloud security becomes easy when you start with real-world examples and attack paths instead of theory. Beginners should focus on understanding misconfigurations, IAM basics, and common cloud vulnerabilities before moving to advanced topics.
Do I need cloud certifications to start cloud security?
Not at the beginning. Certifications can help later, but hands-on learning and practical understanding matter more initially. Many bug bounty hunters and cloud security professionals start without certifications and build skills through practice.
Can beginners earn from bug bounty using cloud vulnerabilities?
Yes. Cloud misconfigurations like exposed S3 buckets, IAM issues, and SSRF vulnerabilities are highly rewarded in bug bounty programs. Beginners who understand these attack paths can earn faster compared to traditional vulnerabilities.
What cloud platform should beginners learn first?
AWS is the most popular choice globally and in India, making it ideal for beginners. Learning AWS fundamentals also makes it easier to understand Azure and GCP later.
Where can beginners learn cloud security for free?
Beginners can start with:
Free blogs and guides on Bugitrix.com
Community learning via Bugitrix Telegram channel
Hands-on labs and beginner-friendly walkthroughs
These resources focus on real-world cloud attacks explained simply.
Final Thoughts: Think Like a Hacker, Secure Like a Pro
Cloud breaches don’t start with hackers being smart.
They start with defenders being careless.
If you understand:
How attackers think
How misconfigurations connect
How attack paths form
👉 You’re already ahead of 90% beginners.
Keep learning.
Stay curious.
Build skills that matter.
Welcome to the hacker mindset — the ethical way. 🛡️
— Team Bugitrix 💙
