Introduction – Why Thinking Like an Attacker Changes Everything

Most people learn cybersecurity by memorizing tools, commands, or vulnerability names. Attackers don’t.
They start with questions, not tools.
What can I see from the outside?
What assumptions did the developer make?
Where will security be weakest because it was “trusted”?
This difference in thinking is why many organizations deploy strong defenses yet still get breached. Security fails not because controls don’t exist, but because defenders think in rules while attackers think in opportunities.
In offensive security, success comes from understanding how attackers reason, not just what they exploit. Attackers don’t try to break everything. They look for the cheapest path to impact—the smallest mistake that leads to the biggest gain.
⚠️ Critical mindset shift:
Attackers are not magicians. They are opportunists.
In this guide, you’ll learn how attackers:
Analyze systems from an outsider’s perspective
Spot weaknesses defenders ignore
Chain small issues into real-world compromises
This matters in the real world because:
Blue teams who think offensively detect attacks earlier
Bug bounty hunters who adopt attacker logic find higher-impact bugs
Security professionals who understand attacker psychology design stronger defenses
🔐 Skill level: Beginner
No prior hacking experience is required. Concepts will be explained in simple language, without sacrificing technical accuracy.
By the end of this article, you won’t just know what attackers do—you’ll understand why they do it, which is the foundation of ethical hacking, red teaming, and real-world cybersecurity.
People Also Ask – Common Questions About Attacker Mindset
Why is thinking like an attacker important in cybersecurity?
Thinking like an attacker helps security professionals:
Identify real-world risks earlier
Find vulnerabilities scanners miss
Understand breach reports more clearly
Design stronger, more resilient systems
Most successful attacks exploit logic and mindset gaps, not just technical flaws.
Can beginners learn the attacker mindset without hacking experience?
Yes. The attacker mindset is about how you think, not what tools you use. Beginners can start by:
Asking “what if?” questions
Understanding how systems are designed
Learning how trust and assumptions work
Tools come later; mindset comes first.
Is attacker thinking only useful for ethical hackers and bug bounty hunters?
No. This mindset is valuable for:
Blue team defenders
SOC analysts
Cloud security engineers
Developers
Security architects
Anyone responsible for protecting systems benefits from understanding how attackers approach targets.
Do attackers always use advanced exploits?
No. Most real-world attacks rely on:
Misconfigurations
Weak access controls
Exposed assets
Business logic flaws
Attackers prefer the simplest path to impact, not the most complex exploit.
Core Concepts – The Attacker Mindset Explained

Before touching tools, payloads, or exploits, attackers build a mental model of the target. This mindset is what separates random scanning from meaningful compromise. Offensive security begins in the brain, not the terminal.
What Does “Thinking Like an Attacker” Really Mean?
Thinking like an attacker means looking at systems the way they were never intended to be used.
Defenders ask:
Is this secure?
Does this meet policy?
Did we block known attacks?
Attackers ask:
What happens if I use this feature incorrectly?
What did the developer assume I would never do?
Where is security relying on trust instead of verification?
Attackers don’t care about:
Best practices
Compliance checklists
Documentation
They care about outcomes.
If a system behaves in a way that gives them access, data, or control—even indirectly—that’s a win.
🔐 Key attacker traits:
Curious, not reckless
Lazy but efficient
Focused on leverage, not perfection
Attackers prefer one weak link over ten strong controls. They look for:
Forgotten endpoints
Over-trusted roles
Features never reviewed for abuse
⚠️ Common misconception:
Attackers don’t “hack harder” — they think differently.
Attacker Goals: Access, Control, Impact
Almost every real-world attack can be traced back to three core goals. Understanding these goals helps you predict attacker behavior before it happens.
1. Access
This is the initial foothold.
User account
API token
Internal endpoint
Low-privilege role
Attackers don’t need admin access immediately. Any access is valuable if it can be expanded later.
2. Control
Once inside, attackers try to:
Escalate privileges
Move laterally
Maintain persistence
This is where misconfigurations, weak permissions, and trust relationships get abused.
3. Impact
The final objective depends on motivation:
Data theft
Account takeover
Financial fraud
Service disruption
💻 Real-world insight:
Many breaches start with “low severity” issues that defenders ignore, but attackers patiently chain together.
| Attacker Goal | What They Look For | Simple Example |
|---|---|---|
| Access | Weak entry points | Open signup abuse |
| Control | Excessive permissions | User → admin escalation |
| Impact | Valuable assets | Database exfiltration |
🔐 Skill level: Beginner
These concepts apply to web apps, APIs, cloud, mobile, and internal networks alike.
Why This Mindset Matters in Offensive Security
If you only learn vulnerabilities, you’ll always depend on scanners and tools.
If you learn attacker thinking, you can:
Find bugs others miss
Understand breach reports instantly
Design defenses that fail safely instead of catastrophically
This mindset is the foundation for:
Ethical hacking
Bug bounty hunting
Red team operations
Threat modeling
Secure system design
Attackers don’t see systems as “secure or insecure.”
They see them as useful or useless.
And the moment a system becomes useful to an attacker, security has already failed.
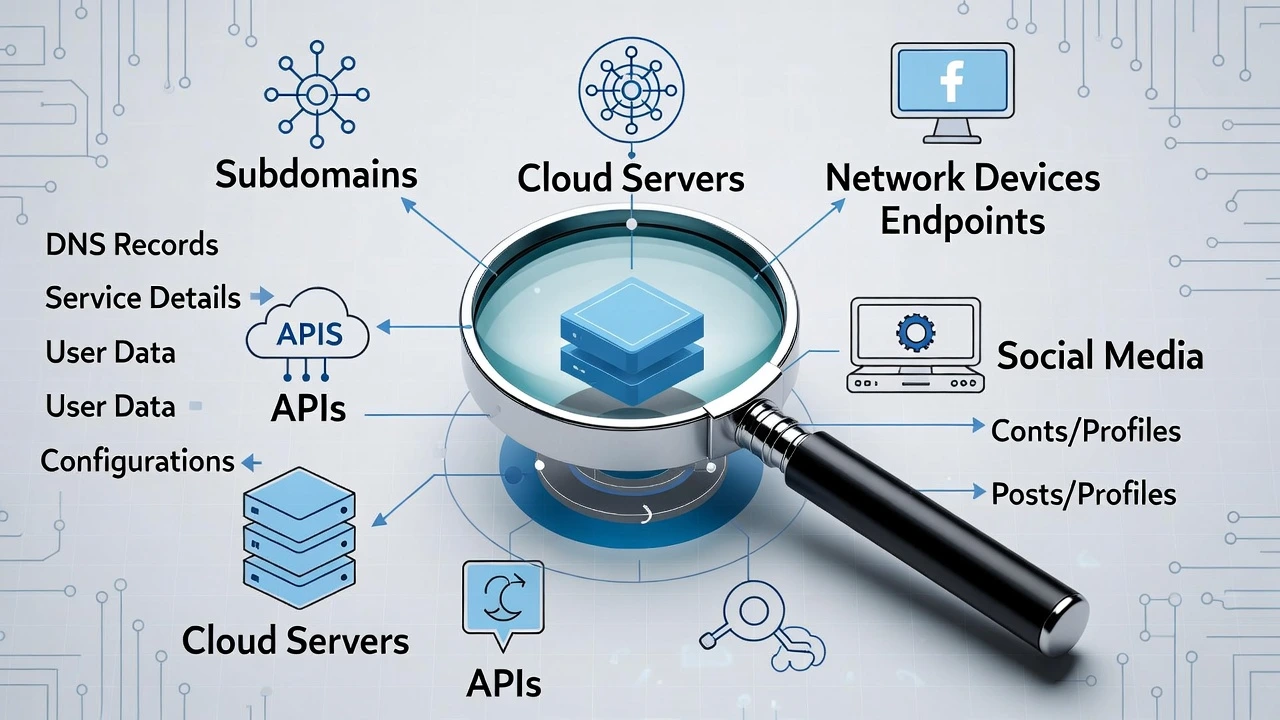
Reconnaissance – Seeing What Defenders Miss
Reconnaissance is the art of learning without touching—and when touching is required, doing it quietly.
Attackers start by asking:
What is publicly visible?
What exists but isn’t documented?
What changed recently?
They gather information long before attempting exploitation.
Two Types of Reconnaissance
Passive Recon
No direct interaction with the target
Uses public data and metadata
Leaves no obvious traces
Examples:
DNS records
Subdomains
Public repositories
Error messages indexed by search engines
Active Recon
Direct interaction with the system
Carefully measured to avoid detection
Used to confirm assumptions
Examples:
Endpoint probing
Parameter discovery
Behavior testing
🔐 Why this matters:
Most attacks succeed because defenders don’t know what’s exposed. Attackers always do.
⚠️ Common defender mistake:
Assuming “unknown” assets are protected because they aren’t advertised.
Attack Surface Mapping – Finding Weak Entry Points
After recon, attackers organize everything into an attack surface map.
They don’t see:
One application
One server
One login page
They see entry points.
Attackers ask:
Which inputs accept user control?
Which features rely on trust?
Which paths were added quickly and never reviewed?
High-Value Entry Points Attackers Love
Authentication flows
File uploads
APIs
Admin panels
Integrations with third-party services
🔐 Attacker checklist mindset:
Can I access this without authentication?
Can I access it with the wrong role?
Can I manipulate inputs the system trusts?
💻 Real-world insight:
Most critical vulnerabilities are found in business logic, not exotic exploits.
Exploitation Logic – Abusing Trust, Not Just Bugs
Exploitation is not about breaking code—it’s about breaking assumptions.
Attackers look for places where developers assumed:
Users will behave correctly
Requests will follow the UI flow
Roles won’t be misused
They test what happens when those assumptions fail.
Examples of Exploitation Logic
Changing IDs to access other users’ data
Skipping steps in a multi-step process
Replaying requests in the wrong order
Using valid features in unintended ways
⚠️ Important warning:
If a feature works exactly as designed but allows abuse, attackers still win.
Attackers don’t care whether something is:
“Out of scope”
“Not intended”
“Low severity”
They only care whether it:
Gives access
Increases control
Moves them closer to impact
🔐 Skill level: Intermediate
This is where mindset begins to outperform tools.
Advanced Insights – How Skilled Attackers Chain Everything Together
Beginner attackers look for single vulnerabilities.
Skilled attackers look for paths.
This is where real-world breaches happen—not because of one critical bug, but because multiple small weaknesses are connected into a complete attack story.
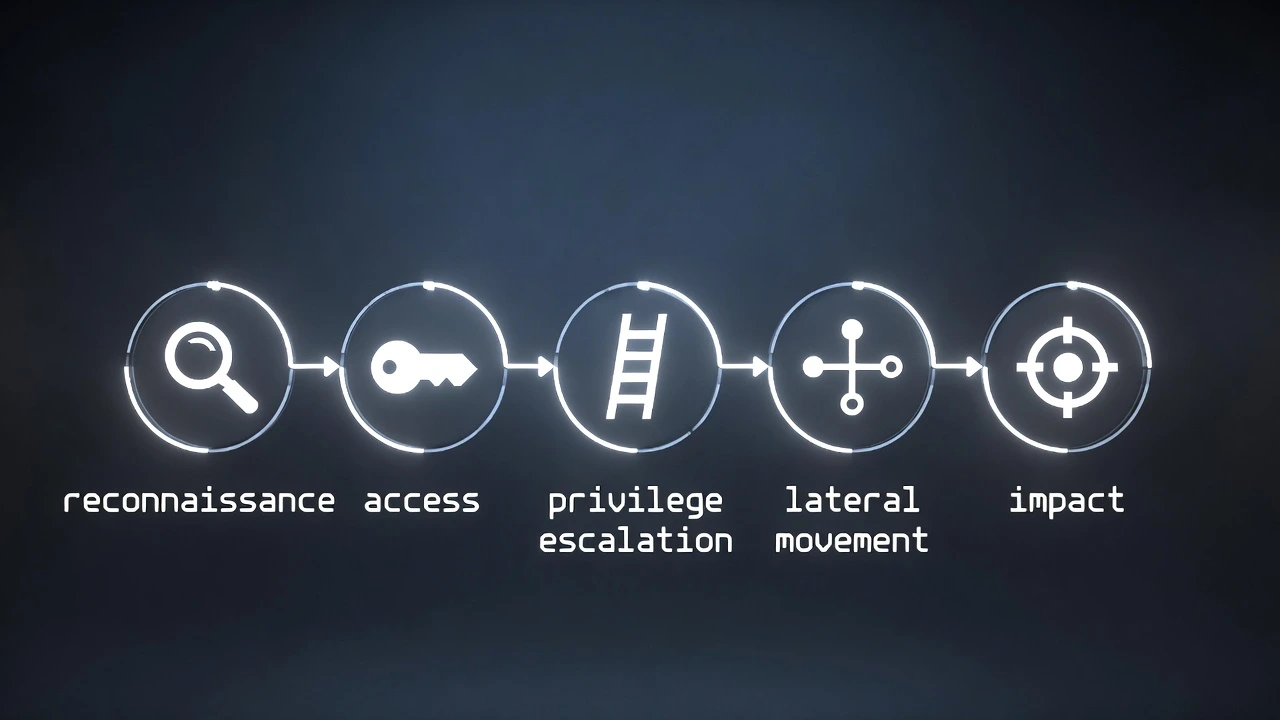
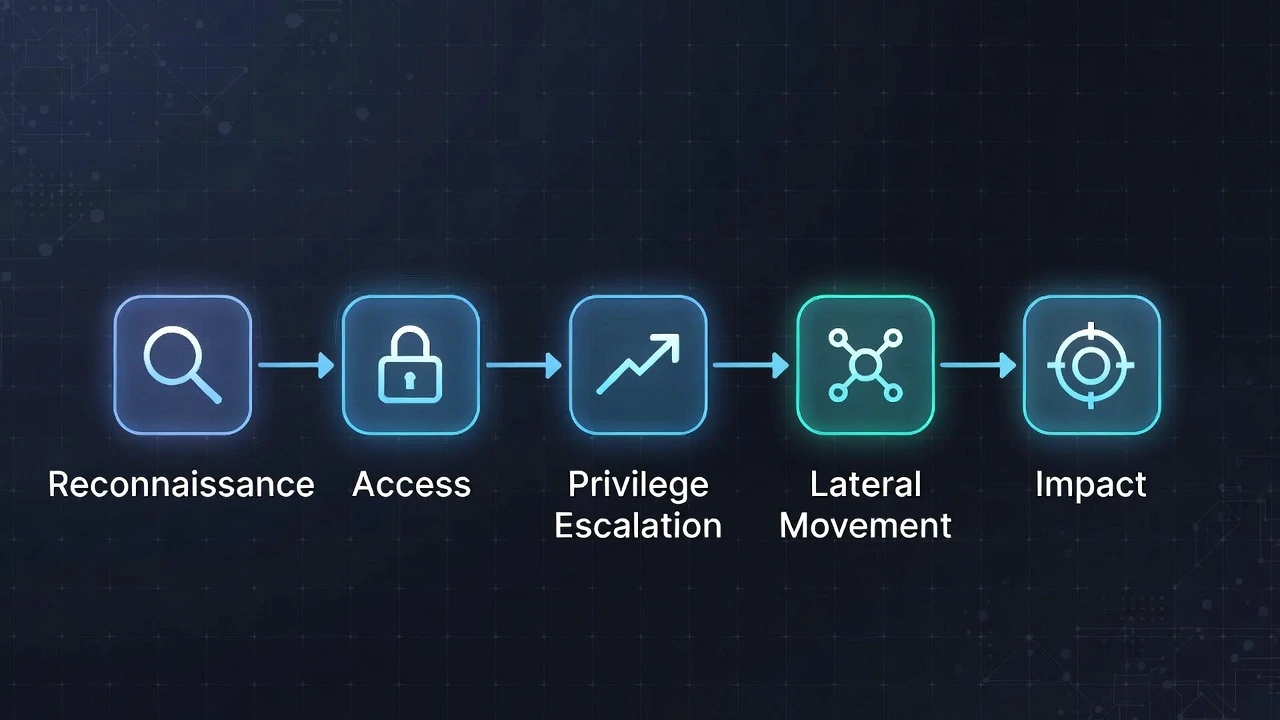
Kill Chains & Attack Paths
A kill chain is the attacker’s roadmap from first contact to final impact. Each step may look harmless on its own, but together they form a full compromise.
Typical attacker thinking:
This alone isn’t enough… but what if I combine it with that?
Where does this access lead next?
What trust relationships can I abuse?
Simplified Attack Kill Chain
Reconnaissance – Identify exposed assets
Initial Access – Gain a foothold
Privilege Escalation – Increase permissions
Lateral Movement – Access other systems
Persistence – Maintain access
Impact – Achieve final objective
🔐 Why this matters:
Defenders often fix individual issues without seeing how they connect.
⚠️ Reality check:
Removing one vulnerability does not break the chain if alternate paths exist.
Thinking in Chains, Not Single Vulnerabilities
Attackers treat vulnerabilities like building blocks.
A low-severity issue becomes dangerous when it:
Exposes internal data
Leaks identifiers
Reveals system behavior
Enables enumeration
These “small” issues help attackers:
Plan next moves
Reduce guesswork
Avoid detection
💻 Bug bounty reality:
Many high-paying reports are not “critical bugs” but well-explained chains showing clear impact.
Attackers ask:
What does this give me next?
Can I repeat this at scale?
Can I turn this into something persistent?
🔐 Skill level: Advanced
This mindset separates surface-level testing from real offensive security.
Red Team vs Real Attackers – What’s Different?
Red teams simulate attackers—but real attackers have fewer rules.
| Red Team | Real Attacker |
|---|---|
| Scoped | No scope |
| Time-limited | Patient |
| Controlled | Opportunistic |
| Report-driven | Impact-driven |
🔐 Why this matters:
Security teams often prepare for audits, not adversaries.
Real attackers:
Wait months
Abuse business logic
Exploit human behavior
Return after patches
⚠️ Key insight:
Compliance does not equal security. Thinking like an attacker exposes what audits miss.
Conclusion – Train Your Mind Before Your Tools
Tools change. Techniques evolve.
But the attacker mindset stays consistent.
Attackers don’t win because they have better exploits—they win because they:
Question assumptions
Look for shortcuts
Chain small weaknesses into big outcomes
If you only learn tools, you’ll always be one step behind.
If you learn how attackers think, you can predict behavior, find deeper issues, and build security that survives real-world abuse.
🔐 Key takeaways to lock in the mindset:
Attackers think in goals, not vulnerabilities
Reconnaissance is where most battles are won
Business logic flaws are more dangerous than flashy exploits
Low-severity issues become critical when chained
Defensive security improves when designed offensively
For ethical hackers and bug bounty hunters, this mindset helps you:
Find impactful vulnerabilities others miss
Communicate risk clearly
Grow from tool user to security thinker
For defenders and security professionals, it helps you:
Anticipate attacks instead of reacting
Reduce breach impact
Build systems that fail safely, not catastrophically
💻 Final reality check:
Security is not about stopping attackers—it’s about understanding them better than they understand your systems.
Frequently Asked Questions (FAQ)
What is offensive security in simple terms?
Offensive security is the practice of thinking and testing like an attacker to find weaknesses before real attackers do. It focuses on identifying how systems can be abused rather than just checking if rules are followed.
Is learning how attackers think legal and ethical?
Yes—when done responsibly. Ethical hacking, bug bounty hunting, and red teaming are all legal when performed:
With permission
Within scope
For defensive improvement
The goal is prevention, not harm.
How long does it take to develop an attacker mindset?
The basics can be learned quickly, but mastery takes time. Progress depends on:
Hands-on practice
Studying real-world breaches
Reviewing vulnerability reports
Constantly asking “how could this be abused?”
Mindset improves with experience, not memorization.
What skills help develop attacker thinking faster?
Key skills include:
Curiosity
Logical reasoning
Understanding system design
Basic networking and web concepts
Ability to think in steps and chains
Tools enhance skills, but mindset drives results.
Why do low-severity issues matter to attackers?
Because attackers chain vulnerabilities. A low-severity issue can:
Leak information
Enable enumeration
Reduce guesswork
Open paths to bigger compromises
Attackers rarely rely on a single vulnerability.
Can this mindset help developers write more secure code?
Absolutely. Developers who think like attackers:
Anticipate misuse
Validate trust boundaries
Reduce logic flaws
Build safer workflows
This leads to more secure applications from the start.
🚀 Ready to Start Thinking Like an Attacker?
If you truly want to grow in cybersecurity, tools alone won’t get you there — mindset will.
At Bugitrix, we help you:
Learn offensive security the way real attackers think
Understand bugs, misconfigurations, and logic flaws in simple language
Build skills that actually work in bug bounty, red teaming, and real-world security
🔐 Join our growing hacker community
👉 Telegram: https://t.me/bugitrix — daily insights, mindset breakdowns, and real attack thinking
🌐 Website: https://bugitrix.com — blogs, resources, and upcoming learning content
📩 Newsletter: Get practical offensive security lessons straight to your inbox
Don’t just learn what vulnerabilities are.
Learn how attackers find and abuse them — before they do. 💻