Introduction

Cybersecurity in 2026 is moving faster than ever — and attackers are evolving just as quickly. From one-click AI exploits to silent website takeovers, today’s threats don’t rely on noisy malware or obvious mistakes. They exploit trust, automation, and overlooked misconfigurations.
In this Bugitrix breakdown, we cut through the noise and analyze the most critical cybersecurity incidents making headlines right now. No fear-mongering. No fluff. Just real attacks, real impact, and real lessons from a hacker’s perspective — so builders, defenders, and learners can stay one step ahead.
Welcome to the front line of modern cybersecurity. 🔐⚡
📰 News #1: The One-Click Attack That Exposed Microsoft Copilot Users
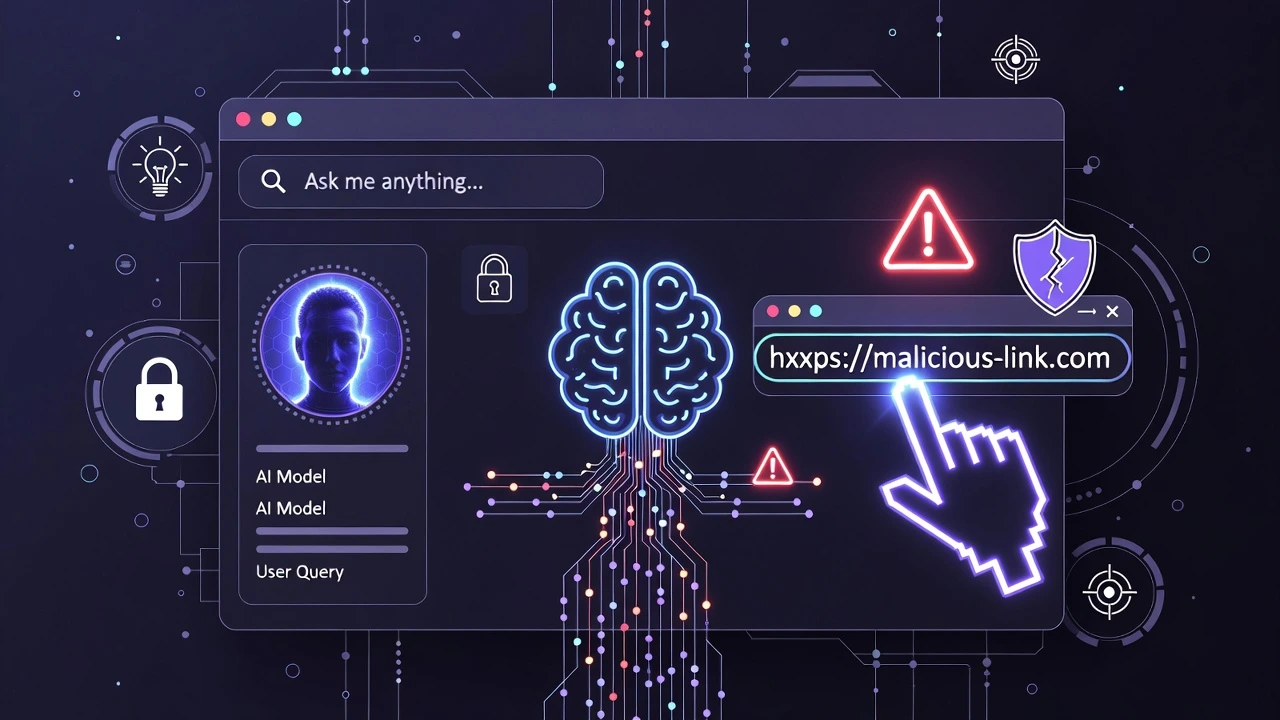
In the world of AI-powered productivity, Microsoft Copilot has become a daily companion for millions. But January 2026 delivered a harsh reminder: even AI assistants can become attack surfaces.
Security researchers uncovered a critical vulnerability dubbed “Reprompt”, a one-click attack technique that allowed attackers to steal entire Copilot conversation histories simply by tricking users into clicking a seemingly legitimate link. No malware downloads. No suspicious pop-ups. Just one click — and the attacker gained access to sensitive AI interactions.
This attack worked by abusing how Copilot processed external links and contextual prompts. Once triggered, attackers could silently extract data that users believed was private, including business discussions, internal ideas, and sensitive prompts shared with the AI.
To Microsoft’s credit, the issue was patched quickly after responsible disclosure. But the damage was already done — proving once again that human trust is still the weakest link in cybersecurity.
🧠 Bugitrix Insight
At Bugitrix, we say it loud and clear:
AI doesn’t get hacked — users do.
This incident reinforces a core hacker lesson: never blindly trust links, even when they look clean, branded, or “AI-approved.” Whether it’s Copilot, ChatGPT, or any other AI tool, attackers will always hunt for logic flaws before technical ones.
Rule of thumb:
If a link matters, type it manually. One click can be the difference between productivity and compromise.
📰 News #2: WordPress Sites Hijacked via Actively Exploited Plugin Flaw
If you run a WordPress website, January 2026 came with a red alert.
A critical vulnerability (CVE-2026-23550) was discovered in the Modular DS plugin, a tool installed on 40,000+ WordPress websites worldwide. What makes this flaw especially dangerous is its simplicity — attackers don’t need a password to take over vulnerable sites.
Even worse?
This vulnerability is actively being exploited in the wild.
Attackers are using it to gain administrative control, inject malicious content, redirect traffic, and in some cases, fully weaponize compromised websites for phishing and malware distribution.
For businesses, bloggers, and developers alike, this exploit highlights a painful truth:
Your website is only as secure as its weakest plugin.
🧠 Bugitrix Insight
From a hacker’s perspective, WordPress plugins are gold mines. One vulnerable plugin can open thousands of doors at once — and attackers know this.
If you manage WordPress sites, here’s the non-negotiable rule:
Audit your plugins
Update immediately
Remove anything unused
Better yet, enable automatic updates and treat plugin security like patching a production server — because that’s exactly what your website is.
At Bugitrix, we train ethical hackers and defenders to think like attackers. And attackers love outdated WordPress plugins.
📰 News #3: Fake Browser Extensions Hijacking Corporate Accounts
Browser extensions are supposed to boost productivity — but attackers are turning them into silent backdoors.
Security researchers uncovered five malicious Google Chrome extensions impersonating well-known enterprise platforms like Workday and NetSuite. These fake extensions looked legitimate, functioned normally on the surface, and blended perfectly into corporate workflows.
Once installed, the extensions hijacked active login sessions, allowing attackers to gain unauthorized access to enterprise accounts without triggering password alerts or MFA challenges. In simple terms: users unknowingly handed over authenticated access to their work systems.
This attack is particularly dangerous in corporate environments, where a single compromised browser session can lead to lateral movement across internal tools, HR systems, and financial platforms.
🧠 Bugitrix Insight
From a hacker’s perspective, browser extensions are a dream target — persistent, trusted, and rarely audited.
At Bugitrix, we emphasize that endpoint security doesn’t stop at antivirus. Extensions should be treated like installed software:
If you didn’t install it intentionally, remove it
If you don’t actively use it, delete it
If it asks for excessive permissions, it’s a red flag
One malicious extension is all it takes to bypass months of security hardening.
📰 News #4: Chinese State-Linked Hackers Target North American Infrastructure
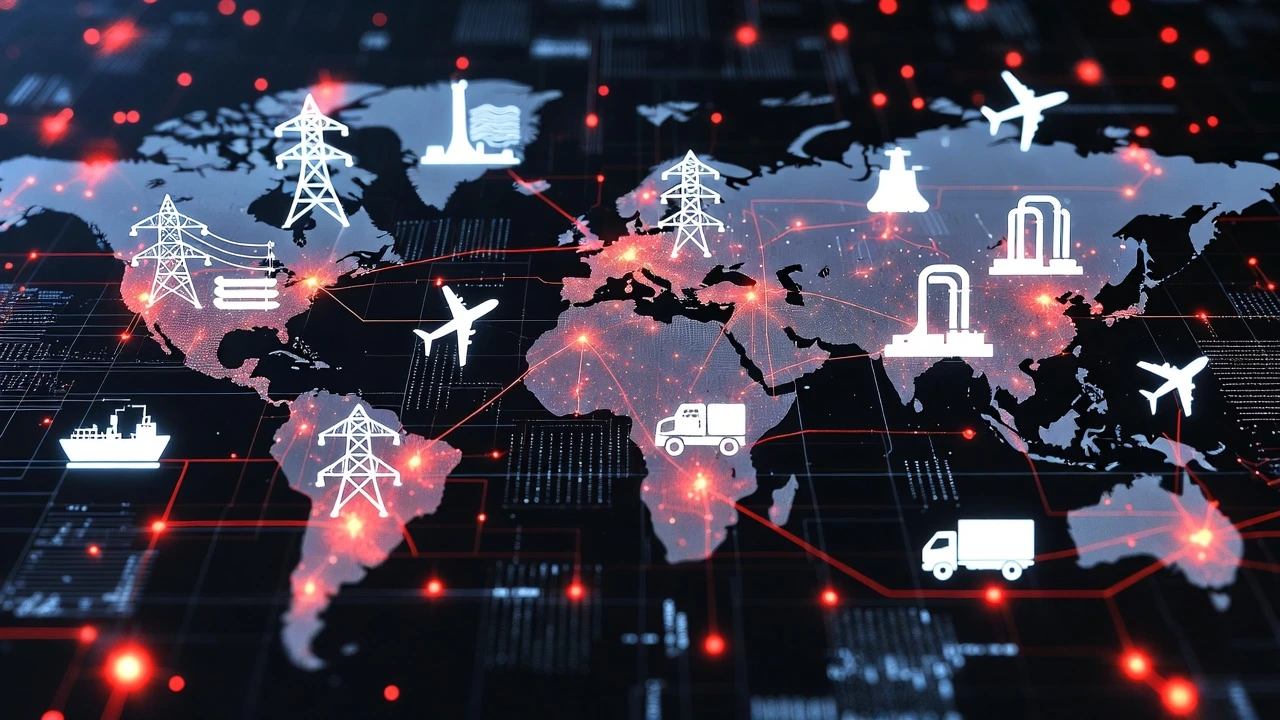
This isn’t about individual users — this is about national-scale cyber warfare.
A threat group identified as UAT-8837, believed to be linked to Chinese state interests, has been actively targeting critical infrastructure across North America since at least 2025. Their focus includes systems tied to energy, water, transportation, and essential services.
The attackers relied heavily on open-source tools and credential-theft techniques, allowing them to quietly harvest passwords and security data while avoiding detection. Rather than loud ransomware attacks, this campaign prioritized long-term access and intelligence gathering.
These kinds of operations are designed to sit silently inside networks — mapping systems, understanding dependencies, and preparing for future leverage.
🧠 Bugitrix Insight
Advanced hackers don’t always break things — sometimes they just wait.
This incident highlights why cybersecurity isn’t just an IT problem. It’s a public safety issue. Infrastructure systems were never designed for modern threat actors, yet they’re now prime targets.
At Bugitrix, we teach that true defense means assuming compromise and monitoring behavior, not just blocking malware.
📰 News #5: Ransomware Groups Continue to Dominate the Threat Landscape

Despite takedowns, arrests, and sanctions, ransomware is still thriving.
On January 16, multiple organizations were hit by well-known ransomware groups including Qilin, Akira, LockBit, and INC_RANSOM. Victims ranged from law firms to healthcare providers, proving once again that no industry is off-limits.
Ransomware remains effective because it attacks what organizations value most: availability and data. Once systems are encrypted, attackers apply pressure through downtime, data leaks, and reputational damage — forcing victims into impossible decisions.
The persistence of these groups shows that ransomware isn’t going away. It’s evolving, professionalizing, and scaling.
🧠 Bugitrix Insight
Ransomware succeeds not because it’s advanced — but because basic defenses still fail.
From a hacker mindset, most ransomware infections begin with:
Unpatched systems
Weak credentials
Phishing emails
Poor backup strategies
At Bugitrix, we drill one rule relentlessly:
If your backups aren’t tested, you don’t have backups.
Ransomware isn’t a “what if” scenario anymore. It’s a when.
📰 News #6: Instagram Data Breach Claims Raise Serious Questions

Mid-January sparked panic across social media when a hacker claimed on BreachForums that data from 17.5 million Instagram accounts had been exposed. Around the same time, thousands of users reported receiving unexpected password reset emails from Instagram, adding fuel to the fire.
Meta, Instagram’s parent company, did not confirm any internal breach, stating there was no evidence of a compromise within their systems. This has led researchers to believe the exposed data may have originated from third-party sources, credential stuffing campaigns, or older leaked databases being recycled.
Even without official confirmation, the incident highlights a recurring issue: attackers don’t always need to breach a platform directly to compromise users.
🧠 Bugitrix Insight
From a hacker’s perspective, reused passwords are low-hanging fruit.
Most large-scale “social media breaches” today aren’t true breaches — they’re credential reuse attacks powered by leaked data from other platforms. If users recycle passwords, attackers can walk straight in.
Bugitrix rule:
Change passwords regularly
Never reuse credentials
Enable two-factor authentication (2FA) everywhere
No exploit beats bad password hygiene.
📰 News #7: China Bans US and Israeli Cybersecurity Software
Cybersecurity just became even more political.
China issued an order instructing domestic organizations to stop using cybersecurity software from the United States and Israel, citing national security concerns. This move reflects a broader strategy of technological self-reliance and tighter control over national digital infrastructure.
This isn’t about software quality — it’s about trust, sovereignty, and geopolitical influence. Governments are increasingly treating cybersecurity tools as strategic assets rather than neutral technology.
The result? A fragmented global security ecosystem where software choice can be dictated by politics, not protection.
🧠 Bugitrix Insight
Cybersecurity isn’t just code — it’s power.
From an offensive security viewpoint, supply-chain trust is now a frontline issue. Who builds your security tools matters just as much as how they work.
At Bugitrix, we emphasize understanding where tools come from, how they’re maintained, and who controls updates. In modern cyber warfare, software origin can be a threat model of its own.
📰 News #8: Former CISA Director Takes the Helm at RSA Conference

Not all the news is bad — and this one matters.
Jen Easterly, former Director of the Cybersecurity and Infrastructure Security Agency (CISA), has been appointed as the new CEO of the RSA Conference, one of the most influential cybersecurity events in the world.
Easterly is widely respected for her leadership in protecting U.S. critical infrastructure and promoting public-private cybersecurity collaboration. Her appointment signals a shift toward experience-driven leadership at the highest levels of the cybersecurity industry.
For defenders, researchers, and ethical hackers alike, this is a strong signal that real-world security experience is finally shaping industry direction.
🧠 Bugitrix Insight
Leadership matters in cybersecurity.
Conferences like RSA don’t just showcase tools — they shape conversations, priorities, and funding. Having someone with deep operational experience sends a clear message: security is about resilience, not hype.
At Bugitrix, we see this as a positive step toward grounding cybersecurity education and innovation in reality — where attacks happen, defenses fail, and learning never stops.
📰 News #9: Critical AMD Processor Flaw Threatens Confidential Virtual Machines

Even hardware-level security isn’t immune anymore.
Security researchers disclosed a serious vulnerability in AMD processors that could allow attackers to remotely execute code inside confidential virtual machines (VMs). These VMs are specifically designed to protect sensitive workloads by isolating memory from the host system — making this flaw particularly alarming.
The vulnerability impacts enterprise and cloud environments where confidential computing is used to protect financial systems, healthcare data, and sensitive business operations. If exploited, attackers could bypass isolation controls that organizations rely on as their last line of defense.
AMD has acknowledged the issue and is actively working on mitigations, including firmware and microcode updates.
🧠 Bugitrix Insight
From a hacker’s perspective, hardware bugs are crown jewels.
Software can be patched quickly — silicon cannot. That’s why processor-level vulnerabilities carry long-term risk, especially in cloud infrastructure.
Bugitrix takeaway:
Hardware trust should never be blind trust
Firmware and BIOS updates matter just as much as OS patches
Confidential computing reduces risk — it doesn’t eliminate it
Security starts below the operating system, whether we like it or not.
📰 News #10: React2Shell Vulnerability Puts Nearly 85,000 Websites at Risk
Modern web stacks just took a direct hit.
A critical vulnerability named React2Shell was discovered in React Server Components and Next.js, two technologies that power a massive portion of today’s web. This flaw allows unauthenticated remote code execution, meaning attackers could compromise servers without logging in.
Security researchers estimate that approximately 84,916 websites worldwide are potentially vulnerable, with the majority hosted in the United States. A successful exploit could lead to full server takeover, data theft, or deployment of malware at scale.
This vulnerability is a harsh reminder that popular frameworks are high-value targets — not because they’re weak, but because their blast radius is enormous.
🧠 Bugitrix Insight
Attackers follow adoption, not hype.
If a framework is everywhere, it becomes a priority target. From a bug bounty and offensive security perspective, vulnerabilities like React2Shell are exactly what attackers hunt for: high impact, wide reach, and low friction.
Bugitrix rule for developers:
Patch immediately
Track framework security advisories
Never assume defaults are secure
Your tech stack is part of your attack surface.
🔐 Conclusion: What These Attacks Tell Us About Modern Cybersecurity

Looking across these incidents — from AI exploits and plugin takeovers to hardware flaws and state-sponsored attacks — one truth becomes clear:
Cybersecurity failures are no longer isolated mistakes. They’re systemic.
Attackers don’t need zero-days every time. They exploit:
Trust in tools
Delayed updates
Overlooked configurations
Human habits
Whether it’s a single click in an AI chatbot or a forgotten WordPress plugin, the outcome is the same — compromise at scale.
🧠 Final Thoughts: The Bugitrix Mindset

At Bugitrix, we don’t believe in fear-driven security. We believe in awareness, skills, and attacker-level thinking.
Cybersecurity in 2026 isn’t about installing one more tool. It’s about:
Understanding how attackers think
Treating updates as critical operations
Assuming systems will fail — and planning for it
Continuously learning as the threat landscape evolves
There is no such thing as perfect security. But there is such a thing as being harder to hack than the next target.
Stay curious. Stay updated.
And most importantly — think like a hacker, defend like a pro.
— Bugitrix 🔐⚡